UPDATE! With NetScaler Password Spraying attacks, I have added methods to block without IPREP, and a list of subnets that I have seen taking part with compromised devices. Also, info on how to gather info from NetScaler Console, and sort it with Excel for easier visibility.
Pair this with my Location based blocking examples and you effectively can silo off your environment from unwanted visitors.
The following commands should be run on any NetScaler. Make sure to edit the <your domain here> section to be your registered and owned domain. If you have multiple domains, you can create multiple similar FQDNBlock policies to bind on the individually named appliances.
For example for a Gateway URL of Citrix.website.com your entry would be
add responder policy FQDNBlock “HTTP.REQ.HOSTNAME.SET_TEXT_MODE(IGNORECASE).CONTAINS(\”website.com\”).NOT” DROP -logAction FQDNBLOCKLIST
enable ns feature AppFw RESPONDER
add policy dataset Allow_listIP4 ipv4
add policy dataset Block_listIP4 ipv4
add policy dataset Allow_listIP6 ipv6
add policy dataset Block_listIP6 ipv6
add audit messageaction BLOCKLIST WARNING "CLIENT.IP.SRC + \" was dropped because they are listed in the NetScaler Blocklist\"" -logtoNewnslog YES
add audit messageaction FQDNBLOCKLIST WARNING "CLIENT.IP.SRC + \" was dropped because they are attempting to access the Gateway via IP\"" -logtoNewnslog YES
add responder policy Block_IPs "(CLIENT.IP.SRC.TYPECAST_TEXT_T.CONTAINS_ANY(\"Block_listIP4\") || CLIENT.IP.SRC.TYPECAST_TEXT_T.CONTAINS_ANY(\"Block_listIP6\")) && !(CLIENT.IP.SRC.TYPECAST_TEXT_T.CONTAINS_ANY(\"Allow_listIP4\") || CLIENT.IP.SRC.TYPECAST_TEXT_T.CONTAINS_ANY(\"Allow_listIP6\"))" DROP -logAction BLOCKLIST
add responder policy FQDNBlock "HTTP.REQ.HOSTNAME.SET_TEXT_MODE(IGNORECASE).CONTAINS(\"<your domain here>\").NOT" DROP -logAction FQDNBLOCKLISTJust putty into your NetScalers and copy and paste the above code to be secured. This also will check datasets so you can block additional IP addresses, or relax connectivity for any address that might accidently be on the Reputation Block List. I have seen that when customer subnets for Internet Service Providers get dinged as malicious from viruses or botnets.
The following code can be added to any NetScaler with Premium licensing.
enable ns feature Rep
add audit messageaction Malicious WARNING "CLIENT.IP.SRC + \" was dropped because they are listed in the IPREP Database \"" -logtoNewnslog YES
add appfw policy Ip_Rep_Policy "(CLIENT.IP.SRC.IPREP_IS_MALICIOUS && !(CLIENT.IP.SRC.TYPECAST_TEXT_T.CONTAINS_ANY(\"Allow_listIP4\") || CLIENT.IP.SRC.TYPECAST_TEXT_T.CONTAINS_ANY(\"Allow_listIP6\")))" APPFW_BLOCK -logAction Malicious
To enable this for every VIP on the NetScaler, you would bind the Malicious and Block_IPs policies globally with the following commands.
bind appfw global Ip_Rep_Policy 100 END -type REQ_DEFAULT
bind responder global Block_IPs 100 END -type REQ_DEFAULTTo enable Malicious, Block_IPs, and FQDNBlock for just certain VIPs, just bind it as polices on the desired VIP with the following commands. Modify the <Your Gateway VIP> section to match the name of the Gateway VIPs.
bind vpn vserver <Your Gateway VIP> -policy Block_IPs -priority 100 -gotoPriorityExpression END -type AAA_REQUEST
bind vpn vserver <Your Gateway VIP> -policy Ip_Rep_Policy -priority 100 -gotoPriorityExpression END -type REQUEST
bind vpn vserver <Your Gateway VIP> -policy FQDNBlock -priority 120 -gotoPriorityExpression END -type REQUESTThe following IP Subnets are from ISPs that have many compromised devices that I have taken to blocking. If you do have an individual user that is in these ranges, you can place them in the ALLOW list and that single IP will be able to get through.
bind policy dataset dataset_block_listip4 102.16.0.0 -endRange 102.16.63.254
bind policy dataset dataset_block_listip4 104.207.32.0 -endRange 104.207.63.254
bind policy dataset dataset_block_listip4 104.234.227.0 -endRange 104.234.227.254
bind policy dataset dataset_block_listip4 140.228.21.0 -endRange 140.228.21.254
bind policy dataset dataset_block_listip4 141.98.80.0 -endRange 141.98.81.254
bind policy dataset dataset_block_listip4 141.98.9.171
bind policy dataset dataset_block_listip4 141.98.9.3
bind policy dataset dataset_block_listip4 147.78.47.104
bind policy dataset dataset_block_listip4 147.78.47.160
bind policy dataset dataset_block_listip4 147.78.47.200
bind policy dataset dataset_block_listip4 154.214.1.0 -endRange 154.214.1.254
bind policy dataset dataset_block_listip4 156.228.100.0 -endRange 156.228.119.254
bind policy dataset dataset_block_listip4 156.228.124.0 -endRange 156.228.125.254
bind policy dataset dataset_block_listip4 156.228.76.0 -endRange 156.228.99.254
bind policy dataset dataset_block_listip4 172.86.112.36
bind policy dataset dataset_block_listip4 179.60.147.128
bind policy dataset dataset_block_listip4 179.60.147.250
bind policy dataset dataset_block_listip4 179.61.197.0 -endRange 179.61.197.254
bind policy dataset dataset_block_listip4 181.214.164.55
bind policy dataset dataset_block_listip4 185.28.119.162
bind policy dataset dataset_block_listip4 193.201.232.0 -endRange 193.201.235.254
bind policy dataset dataset_block_listip4 204.93.149.0 -endRange 204.93.149.254
bind policy dataset dataset_block_listip4 208.115.218.90
bind policy dataset dataset_block_listip4 212.56.54.0 -endRange 212.56.54.254
bind policy dataset dataset_block_listip4 213.159.74.31
bind policy dataset dataset_block_listip4 31.43.185.0 -endRange 31.43.185.254
bind policy dataset dataset_block_listip4 37.19.196.0 -endRange 37.19.197.254
bind policy dataset dataset_block_listip4 38.132.105.101
bind policy dataset dataset_block_listip4 38.180.242.193
bind policy dataset dataset_block_listip4 38.180.6.219
bind policy dataset dataset_block_listip4 38.180.6.254
bind policy dataset dataset_block_listip4 38.180.90.70
bind policy dataset dataset_block_listip4 45.135.232.0 -endRange 45.135.232.254
bind policy dataset dataset_block_listip4 45.137.213.64
bind policy dataset dataset_block_listip4 45.140.17.0 -endRange 45.140.17.254
bind policy dataset dataset_block_listip4 45.227.255.0 -endRange 45.227.255.254
bind policy dataset dataset_block_listip4 45.61.158.195
bind policy dataset dataset_block_listip4 45.61.166.167
bind policy dataset dataset_block_listip4 45.89.53.82
bind policy dataset dataset_block_listip4 46.161.27.0 -endRange 46.161.27.254
bind policy dataset dataset_block_listip4 5.182.110.0 -endRange 5.182.110.254
bind policy dataset dataset_block_listip4 5.45.73.13
bind policy dataset dataset_block_listip4 79.127.132.0 -endRange 79.127.132.254
bind policy dataset dataset_block_listip4 81.180.240.0 -endRange 81.180.247.254
bind policy dataset dataset_block_listip4 84.193.52.0 -endRange 84.193.54.254
bind policy dataset dataset_block_listip4 84.239.11.0 -endRange 84.239.16.254
bind policy dataset dataset_block_listip4 84.239.25.0 -endRange 84.239.25.254
bind policy dataset dataset_block_listip4 84.239.29.0 -endRange 84.239.29.254
bind policy dataset dataset_block_listip4 84.239.31.0 -endRange 84.239.41.254
bind policy dataset dataset_block_listip4 84.239.4.0 -endRange 84.239.4.254
bind policy dataset dataset_block_listip4 84.239.43.0 -endRange 84.239.43.254
bind policy dataset dataset_block_listip4 84.239.45.0 -endRange 84.239.45.254
bind policy dataset dataset_block_listip4 84.239.47.0 -endRange 84.239.47.254
bind policy dataset dataset_block_listip4 84.239.49.0 -endRange 84.239.49.254
bind policy dataset dataset_block_listip4 84.239.51.0 -endRange 84.239.51.254
bind policy dataset dataset_block_listip4 84.239.55.0 -endRange 84.239.59.254
bind policy dataset dataset_block_listip4 84.239.6.0 -endRange 84.239.9.254
bind policy dataset dataset_block_listip4 86.104.72.25
bind policy dataset dataset_block_listip4 92.63.197.0 -endRange 92.63.197.254
bind policy dataset dataset_block_listip4 94.232.43.153 To find IP addresses and ranges that are attacking you, enable Gateway Insight with Analytics to your NetScaler Console, and then access the following location to get these attacks.
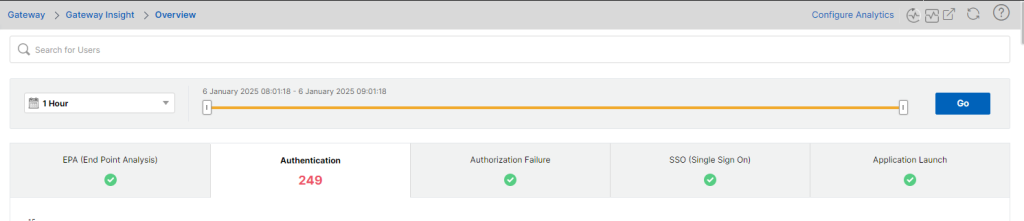
You can export a report from here in tabular CVS format and then process it in Excel. First I will sort the entire list to show me just the “User not found” entries. I will then use the following Advanced Filter against the Client IP Address Field.
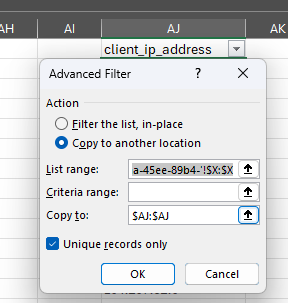
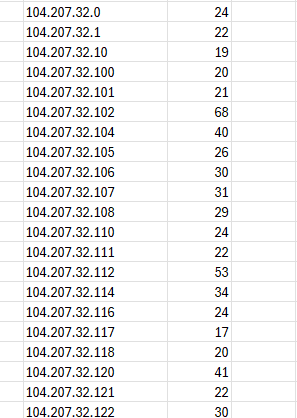
Then, once you have the shortened list, I will use the following formula to give me a count on the entries.
=COUNTIF(X:X,AJ2)This gives you a good idea as to how many times an IP is failing the login.
It’s very easy to tell if someone is being blocked by this IP range, as they will receive a message like this on their browsers.
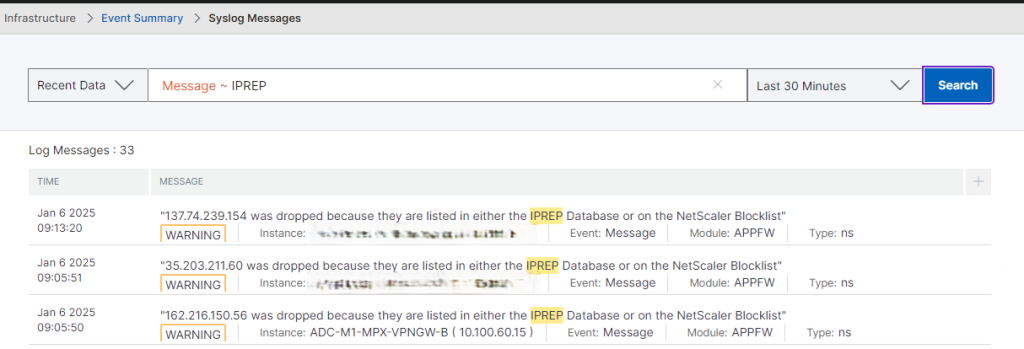
Also within the NetScaler Console you can view the Syslog messages that are generated when IPs are blocked by these policies. You can filter the log down to just WARNING messages and then do a search for IPREP, part of your custom message, or a client’s specific IP ADDRESS in the message field. This is helpful to troubleshoot if you need to ALLOW a single IP from a range that you potentially have in the BLOCKED list.