Most customers are integrating Edge, Office 365, and OneDrive into their non-persistent virtual environments. However to utilize this requires some additional configuration, and if you throw FAS into the mix you need to do some more additional configuration to get the AzureAD PRT working. This guide should provide you the framework to get this setup in your environment.
Azure AD Connect and Zero machine settings
- Azure AD Connect needs to be setup in your environment with Password Hash Synchronization, and Hybrid Azure AD join needs to be configured.
- Your non-persistent maintenance machine needs to have a dsregcmd /leave command executed during sealing to ensure proper image connection. (See my wiki article on maintenance scripts)
- Your non-persistent maintenance machine needs the \Microsoft\Windows\Workplace Join\Automatic-Device-Join scheduled task modified. Add an At Startup Trigger. This will register the machine at it’s startup to Azure AD, and the user account will register with the existing At log on trigger.
Certificate Authority Configuration
- Modify your Citrix_SmartcardLogon to handle Smart Card Logon and Client Authentication
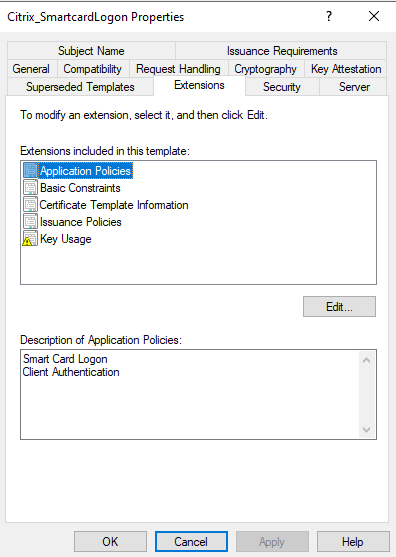
2. Create a webserver that can host your domain CRL. This will needs to be accessible from the Internet on http only.
3. Edit the NTFS permissions on the CRL webservers root to give your Internal Cert Authority Full Control of this folder.
4. Create a windows share to this root directory that gives the Internal Cert Authority servers Read/Write permissions to the folder.
5. Go to properties of your Internal Cert Authority, click Extensions and then click Add.
6. Use file://webserver/share/<CaName><CRLNameSuffix><DeltaCRLAllowed>.crl for the Location.
7. Select Publish CRLs to this location, and Publish Delta CRLs to this location
8. And another extension and use http://outsideurl/<CaName><CRLNameSuffix><DeltaCRLAllowed>.crl for the Location.
9. Select Include in CRLs, Include in the CDP Extension of issued certificates, and Include in the IDP extension of issued CRLs.
10. Right click Revoked Certificates and Publish a new CRL to populate your new distribution.
Azure Active Directory certificate configuration
- Login to portal.azure.com and drill down to Azure Active Directory.
- Click Security
- Click Certificate Authorities
- Click Upload
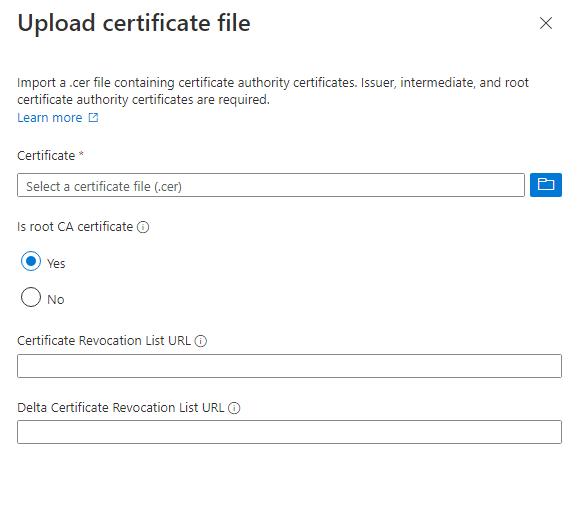
5. Select Authentication Methods on the left hand pane.
6. Select Certificate-based authentication
7. Enable this feature, and restrict it to necessary users if you wish to lock this down further.
Client testing
To verify these settings, login to a non-persistent session with a FAS backed user session.
Open a command prompt and run a dsregcmd /status. You are looking for the following entries to verify it is fully connected.
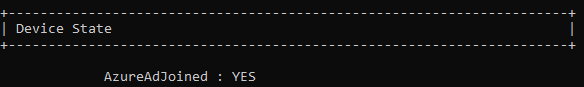
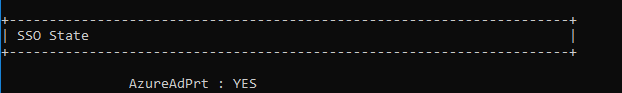
You now should be setup correctly for FSLogix 2210 token functionality, Edge Sync and autologin, Office 365 SSO, and OneDrive autologin with both local authentication and with Federated authentication.
Hi Jeff,
I followed your recommendation settings above, with the exception of the delta CRL. Is this necessary to get PRT token working inside VDI session? I am able to test the Azure CBA by using the O365 login page and selecting the certificate based (user certificate). But when launching VDI, I run the command “dsregcmd /status” and I get error code “AADSTS50017: Validation of given certificate for certificate based authentication failed”. FAS server is configured correctly.
Any help will be appreciate it. Thank you.
Jose
You will either need to setup the CRL for that external access, or disable CRL checking. Also make sure that you have uploaded all of your Root and Intermediate to Azure as well.
Hi, Jeff. Thanks for the super-useful post. Since most of our client organizations would never get (or give) permission to expose an HTTP site to the Internet, where would we instead disable CRL checking? On the FAS server(s)? Elsewhere? More details on this option would be very much appreciated.
That would be disabled in your SAML provider. So in Entra ID case it would be on the Certificate Based Authentication configuration. Since CRL REQUIRES http sites, disabling this check works fine. But make sure to set the lifetime of your FAS certificates to be something low, such as 24 hours, so that revoked certificates are blocked quickly.
Thanks, Jeff. I appreciate the reply.
Hi Jeff,
Great post! I have a use case where Citrix deployment is configured with Okta as IDP and FAS has been deployed to achieve SSON to VDAs (Hybrid joined), however single sign for O365 apps inside FAS enabled VDA fails. We are not using a managed Entra ID domain (hence CBA on EntraID is not an option), it is federated to Okta. As per Citrix documentation , https://docs.citrix.com/en-us/federated-authentication-service/2303/config-manage/aad-sso, if federated to ADFS we need to enable WS-Trust certificatemixed endpoint feature and for any third party IDP they should have a similar feature which can support SSON to 0365 apps while using smart card logon so trying to chase Okta for a similar feature, no luck yet. I wonder if you have any inputs on how to achieve SSON to O365 apps in such scenario?
Did you ever get this figured out? I’m in the exact same situation and I’m not sure which direction to go
Hello Jeff,
Thank you for this post!
Did you configured FAS to make the user certificate available in de Citrix session and do you have any updates or improvements on this solution ?